What is ARP?
The Address Resolution Protocol is a layer 2 network protocol that helps devices discover the MAC Addresses of others and associate them with their IP addresses.
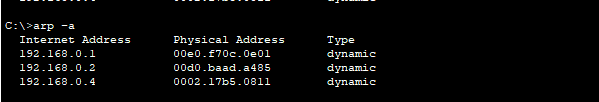
On network devices like routers and switches, this information is stored in MAC address tables. On hosts, it's stored in what is called an ARP cache.
The ARP protocol works by devices broadcasting an ARP request with the target IP address to the network, and getting a reply from the device that has the IP address.
What is ARP Poisoning?
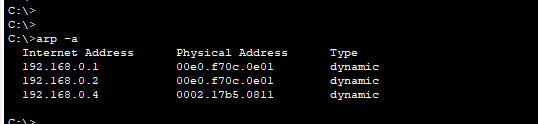
ARP poisoning is a network attack that populates the ARP caches and MAC address tables of devices on a network with spoofed (fake) MAC addresses.
How is it done?
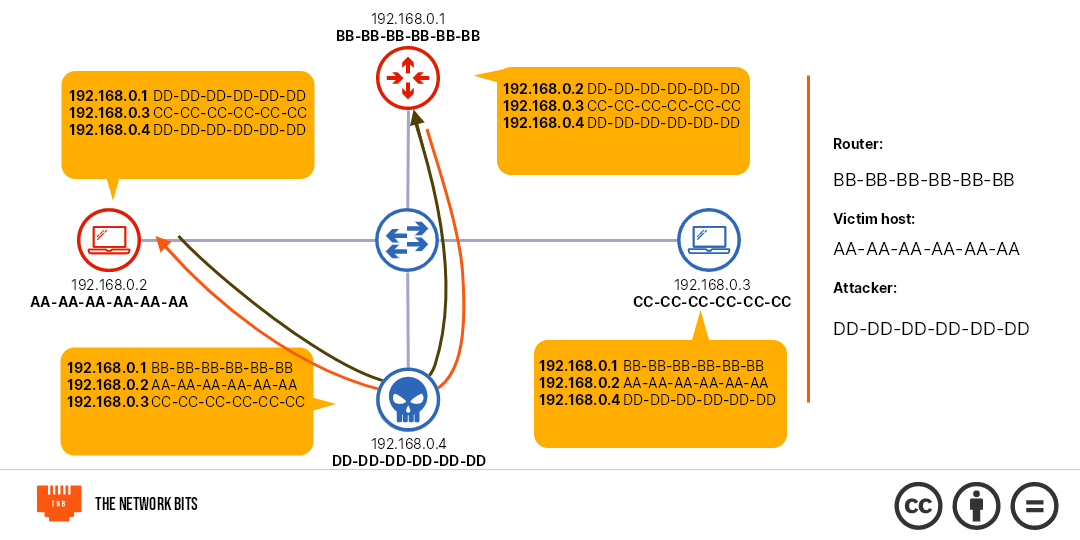
The attack starts with the hacker knowing the devices in the network, either by scanning or some other means. The attacker then sends unsolicited ARP reply messages to the targets with his own MAC address and the IP address of another device.
The target device sees the ARP reply and changes the contents of its ARP cache or MAC address table to suit the new information.
Now, the victim's device maps the IP address of another device to the attacker's MAC address and thereby sends all traffic for that address to the attacker.
What can the attacker achieve by doing this?
The most common way of using this is in a man-in-the-middle (MiTM) attack. Here, the attacker sends spoofed MAC addresses between two devices he wants to intercept. Say a host and the router on a network.
When he's done, both devices send traffic meant for each other to him and he forwards the traffic. This way, he can successfully sniff the traffic and monitor all communications.
In the case where such traffic is not encrypted, he can steal passwords, hijack sessions or inject a malicious payload into the network stream.
Prevention & Solution
Dynamic ARP Inspection: One of the ways to prevent an ARP poisoning attack is by activating DAI on your switches.
With DAI, the switch monitors the ARP packets and anytime an ARP packet is received that conflicts with the already created MAC address table, it drops the packet to prevent the changing of the MAC address table.
Static ARP: ARP caches or MAC address tables can be filled in manually by a network administrator instead of by exchanging ARP messages. This is called static ARP. Using static ARP could help reduce the risk of ARP spoofing.
VPN: VPNs help encrypt traffic to and from your devices. When your traffic is encrypted, it'll prevent anyone who intercepts your traffic from being able to interpret, understand, and manipulate the traffic.
Conclusion
Most network traffic today is encrypted, so attacks like this may not be that harmful or effective. However, it is still a threat, serious or not.
If you got value from this article, please like it, share it, and subscribe to the newsletter. You can also connect with me on LinkedIn or follow The Network Bits on X(Twitter). Thanks.