What is VLAN Hopping, And How Does It Impact Networks?
Securing your VLANs
In this article, we're going to talk about:
What a VLAN is.
Common VLAN hopping methods.
How the attack could impact the networks.
What could be done to mitigate such attacks.
What is a VLAN?
VLANs are a way of separating a network into multiple segments such that devices in a segment cannot communicate with devices in another. This way, the network is more secure and communications between different groups are kept isolated.
This is implemented on switches where the devices are connected to or where access points to the devices are connected.
VLAN Security
There are, however, ways in which this VLAN can be bypassed by malicious actors for the purposes of accessing networks or devices they're prohibited from accessing.
These methods, like many other security threats, take advantage of the weaknesses of the 802.1Q protocol or its implementations in various switches.
The primary two methods are:
Switch spoofing
Double tagging
Switch Spoofing: The Dynamic Trunking Protocol is a protocol that allows switches to automatically configure VLAN trunk ports. These trunk ports allow for trunk links that connect the switch to another switch to enable the movement of packets from one switch to another.
The thing about trunk links is that they allow packets from multiple VLANs to traverse them. They're basically VLAN highways. This makes it ideal for attackers who want to gain access to restricted VLANs.
The attacker can connect a computer or device to the network, make the switch believe it's another switch and then establish a trunk connection with it. Now, he has access to all VLANs.
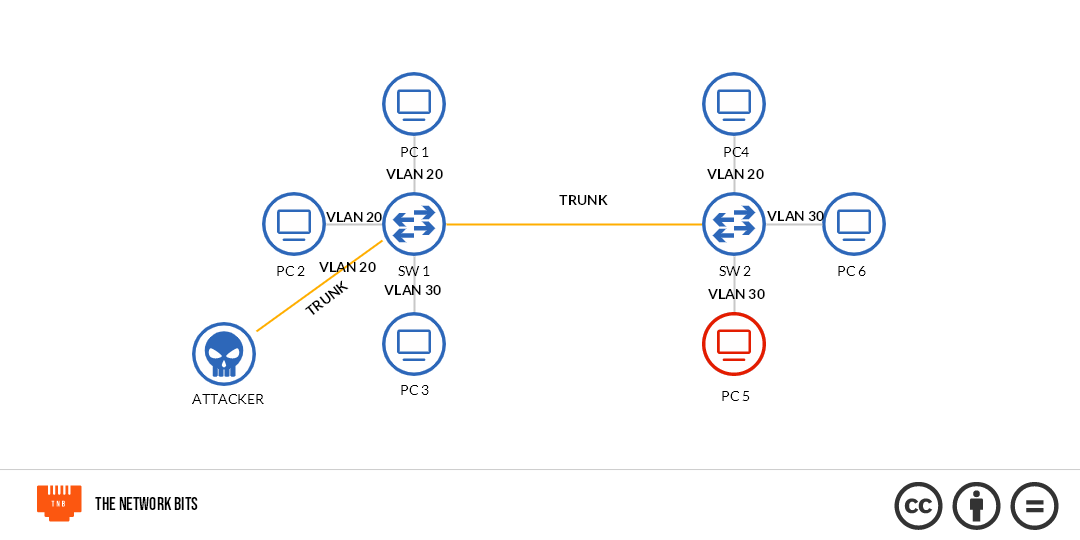
Double Tagging: Double tagging is a method that takes advantage of the native VLAN feature of the IEEE 802.1Q protocol (aka Dot 1Q). The protocol provides for a native VLAN and a default VLAN.
The default VLAN is not the same thing as the native VLAN. VLAN-enabled switches come with a default VLAN which is VLAN 1. This VLAN is not intended to be used as a VLAN in the normal sense, but is a VLAN for every device connected to the switch to reside in whenever there is no VLAN configuration by the network administrator. This VLAN cannot be deleted or modified.
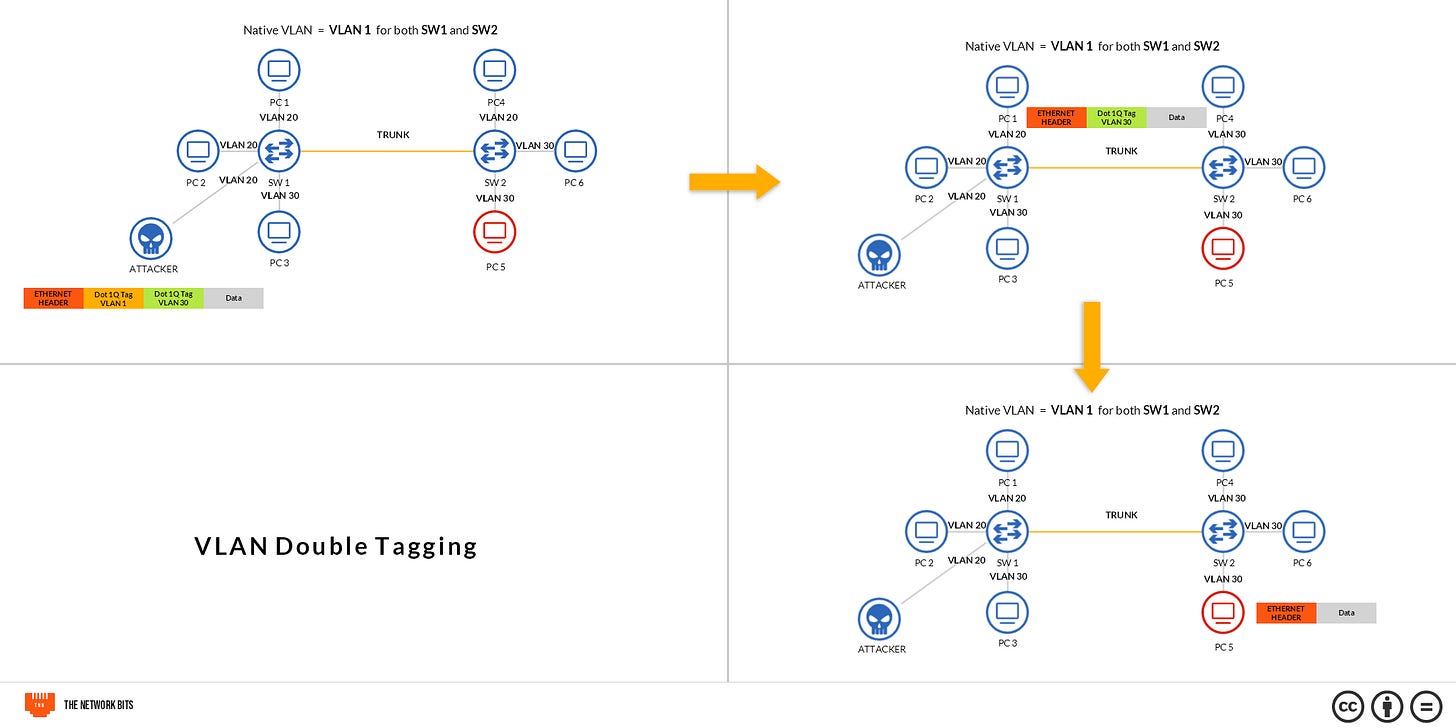
The native VLAN is a VLAN whose packets are allowed to traverse the trunk links without tags. In fact, the switch removes the tags from packets tagged with the native VLAN before forwarding over the trunk links. Double tagging was actually a concept introduced by the IEEE in 2011. It allowed multiple VLAN tags to be inserted in a VLAN frame. However, it allowed for some new exploits.
With double tagging, the attacker creates special packets with a tag to the real VLAN he wants to access. In our case here, it's VLAN 30. Then he wraps those packets in a tag of the native VLAN, which is VLAN 1 by default. When the switch receives the packet, it reads the outer VLAN tag, and because the VLAN ID is that of the native VLAN, it doesn't bother about the Port VLAN ID of the port where it comes from. It just removes the VLAN tag and forwards the packet as is over the trunk. When the packet gets to the next switch, it reads the second tag and the packet reaches the destination.
What if the attacker just added one tag (the destination tag, VLAN 30) to his packet and sent it over the switch? In such a situation, the attacker is connected to a port with a different Port VLAN ID (PVID) from what he wants to connect to. So, traffic would be tagged with the VLAN he resides in, and be dropped because his target VLAN is outside where he's allowed to communicate with.
What damage can such attacks cause to the network?
Traffic that hops VLANs are usually a one-way traffic because the packet sent by the attacker crossed over to a VLAN where it wasn't supposed to be and unless the victim's computer participates in the same kind of network gymnastics the attacker did, there is no way for it to communicate back to the attacker's VLAN. The switch will drop the packet.
The only way that could happen would be if the attacker setup a layer 3 return route for the victim which would circumvent the network the malicious packets already came from.
Because of this, a more practical use of this attacks would be to perform Denial of Service attacks on the victim from another VLAN by overwhelming it with packets.
How to mitigate against VLAN Hopping attacks
Spoofing attacks: The best way to mitigate against spoofing attacks is simply not to use DTP. Just disable the protocol on all switches and configure your ports as access ports. Then, manually configure your trunk ports.
Double tagging: The main reason why attackers can take advantage of your native VLAN is because they know what it is. And they know what it is because you left it at the default setting of VLAN 1.
Therefore, the way to prevent such an attack is to change your native VLAN. Configure it to a random number so that your attackers would have to guess to conduct such an attack. It is important to note that you have to configure the same native VLAN on all the switches in the network for it to work properly.
Summary
VLANs are meant to separate layer 2 networks into different segments. The only way to communicate between two VLANs should be through a layer 3 device (like a router).
VLAN hopping is the act of tricking the switches into allowing packets to move from one VLAN to another without that layer 3 device.
There are two major ways in which that can be done:
Switch spoofing
Double tagging
Some simple steps to mitigate such attacks are:
Always disable the Dynamic Trunking Protocol on your switches.
Configure your access ports and trunk ports manually.
Always change your native VLAN to a random number that shouldn't be easy to guess.
Thank you for reading the article. Don't forget to share the article and subscribe to the newsletter if you enjoyed it. Also do well to comment if you have anything to add or correct. You can also connect with me on LinkedIn or follow The Network Bits on X(Twitter).